The Mission Part 1 - Knock Knock
This challenge was one of 7, which composed the challenge group called "The Mission", which were rated Hard.

The Mission Part 1 - Knock Knock
Published at 5/26/2024, 11:37:00 AM
This challenge was the first of 7 challenges on the same blackbox, which meant we had permission to fuzz and bruteforce if needed.
Upon connecting to the challenge, we are redirected to the url: /app/login , which shows a register button as well. Registering a user was an interesting task, as I could not register from any other domain than nahamcon.ctf. This was a bummer since the app required validation by mail to activate the user account just created.
Upon further enumeration, I noticed /app/logout was redirecting to /dev-app, which opened a new avenue for my progress.

Registering a user there proved more successful and didn’t have validation, which gave me a cookie named dev-token. It took me quite some time before realising that the logout option, if used on the /app side, would actually send a delete request for the correct cookie name for production.
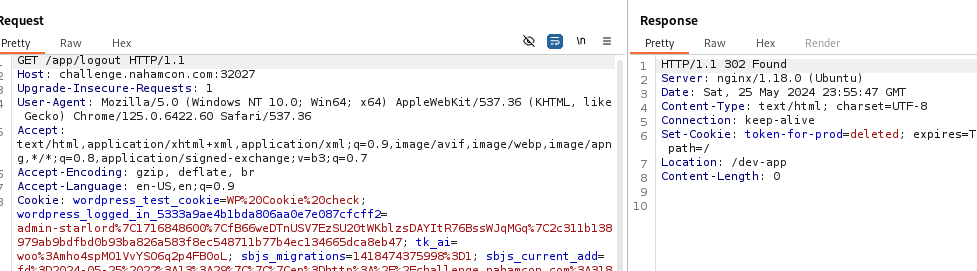
With the correct cookie name, it was then possible to simply reuse the jwt cookie obtained on the dev-app and reuse it in the production app, by changing its name in the browser tools or burp.
token-for-prod=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjozfQ.MVXc0x_5qMYMmU3orSxp7HfC1FOB9FXuutII-AP_eno
With that in hand, we now can be identified as an authenticated user in the dashboard, even though it’s unavailable for maintenance.

Expanding on previous findings, since we now had a username, I wanted to see his details so I visited the following and caught the flag!
/app/api/me

flag{925f2f867c0f46d986979c935aafca31}
Cookies
